Cybersecurity is a sophisticated art. It can truly consume the time and resources of IT teams as they work to safeguard valuable data from the growing risk of cyberattacks and data breaches. The technical nature of it, along with the specific expertise it requires, has created a workforce gap that many fear is nearly impossible to bridge.
By Akshay Bhargava, Chief Product Officer at Malwarebytes
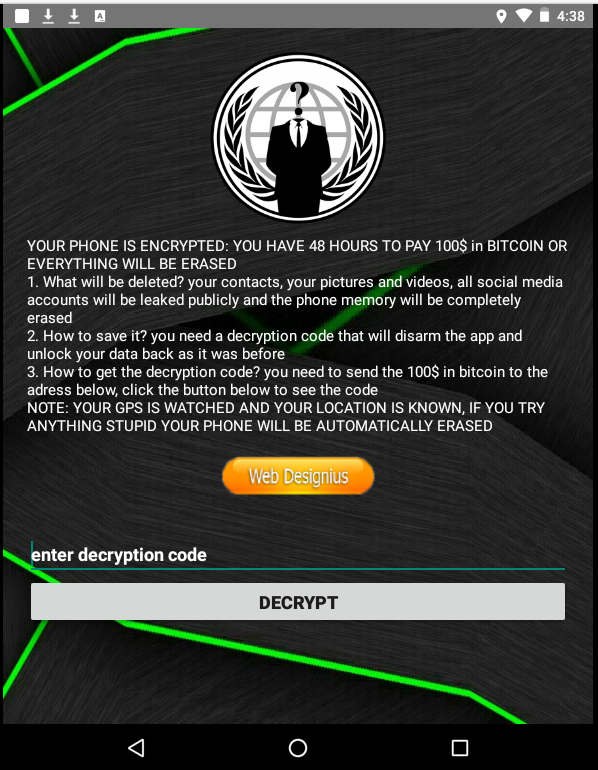
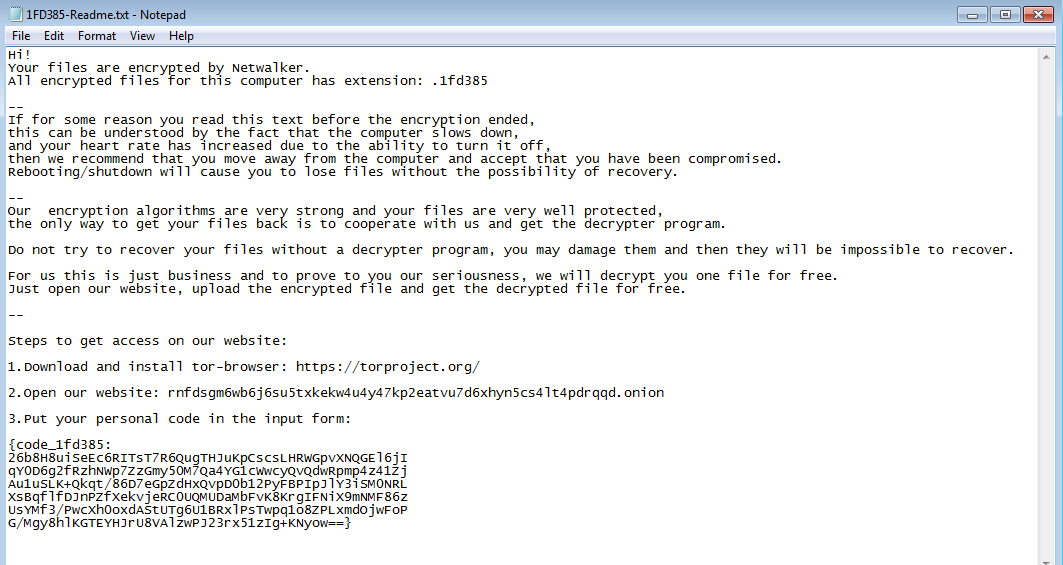
In fact, the cybersecurity workforce gap has been reported to be over four million globally, causing an alarming void of security experts who are fit to protect business and consumer data. This gap is particularly painful for small and midsize businesses (SMBs) where recruiting cybersecurity expertise may be particularly costly or challenging. Unfortunately, with the average cost of a breach weighing in at a hefty $3.92 million, cybersecurity is not something any business – no matter the size – can afford to get wrong. This is especially concerning for SMBs where estimates have found that as many as 60% are forced to shut their doors after a cyberattack.
But the damage caused by a successful attack can extend beyond the SMB itself.
Not only will the SMB suffer in the event of a cyberattack, but the larger enterprises it partners with are also put at risk. Take the 2019 Quest Diagnostics data breach as an example. Nearly 12 million patients were exposed after hackers took control of a payments page for one of Quest’s billing collection vendors, AMCA, exposing account data, social security numbers and health information. The same attack also impacted 7.7 million customers of LabCorp. AMCA has since filed bankruptcy.
It’s also been reported that it was an email attack on a vendor of Target Corp. that exposed the credit card and personal data of more than 110 million consumers in 2013. The Target breach has been traced back to network credentials stolen from an email malware attack on a heating, air conditioning and refrigeration firm used by Target.
In each instance, the exposure of a smaller organization put a much larger enterprise at risk. There is hope though, that if we can democratize cybersecurity, SMBs could realize the same protections enterprises require, and we’d all be much safer as a result.
So, what can be done? How can SMBs achieve a cybersecure environment like their enterprise competitors? The key lies in automation and empowering employees.
Automation Unlocks Cybersecurity Democratization
Adopting security automation is an effective way to achieve cyber resilience without adding staff or cost burden. It’s the core of cybersecurity democratization. In fact, companies that fully deploy security automation realize an average $1.55 million in incremental savings when handling a data breach. Not only will automation relieve the pressure from continued staff and skills resource constraints, it’s also dynamically scalable, always on, and enables a more proactive security approach that makes the business exponentially more secure. When applying automation, consider each of these three critical security process areas:
1. Threat detection and prevention. Technologies including advanced analytics, artificial intelligence and machine learning give SMBs the ability to apply adaptive threat detection and prevention capabilities so that they can stay one step ahead of cybercriminals without added staff. By automating threat detection, powered by strong threat intelligence, SMBs can detect new, emerging threats while also increasing the detection and prevention of known threats that may have previously slipped past corporate defenses. Furthermore, they can reduce the noise from incident alerts and false positives from detection systems, improving overall threat detection and prevention success rates.
2. Incident response. If a successful cyberattack does break through, it can move throughout an environment like wildfire. Incident response time is critical to mitigating the severity of the damage, and for those SMBs impacted by the security skills shortage, having the response team needed to react fast is likely a problem. By automating incident response, organizations can greatly improve their cyber resilience. Adopt solutions that will automatically isolate, remediate and recover from a cyberattack:
- Isolate. By automating endpoint isolation SMBs are able to rapidly contain an infection while also minimizing disruption to the user. Effective isolation includes the automated containment of network, device and process levels. Advanced solutions will also impede malware from “phoning home” which will restrict further damage to the environment.
- Remediate. Automating remediation will quickly and effectively restore systems without requiring staff resource time or expertise. It will also allow CISOs to remediate endpoints at scale to significantly reduce the company’s mean-time-to-response.
- Recover. Finally, incident response should also provide automated restore capabilities to return endpoints to their pre-infected, trusted state. During this recovery process it’s also wise to enable automated detection and removal of artifacts that may have been left behind during the incident. This is essential to preventing malware from re-infecting the network.
3. Security task orchestration. To further relieve security staff while ensuring cyber resiliency, low-level tasks should be automated, including the orchestration between complex, distributed security ecosystems and services. This will ensure a more nimble and responsive environment in the event a cyberattack is successful. Cloud-based management of endpoints can help, specifically if it provides deep visibility with remediation maps…[…] Read more »…..
This article first appeared in CISO MAG.
<Link to CISO MAG site: www.cisomag.com>


















ROLE DESCRIPTION
We are looking for a Membership Manager to join the company and take on one of the most opportunistic roles the industry has to offer. This is a role that allows for you to create and develop relationships with leading solution providers in the enterprise technology space. Through extensive research and conversation you will learn the goals and priorities of IT & IT Security Executives and collaborate with companies that have the solutions they are looking for. This role requires professionalism, drive, desire to learn, enthusiasm, energy and positivity.
Role Requirements:
Role Responsibilities:
Apex offers our team:
Entry level salary with competitive Commission & Bonus opportunities
Apex offers the ability to make a strong impact on our products and growing portfolio.
Three months of hands on training and commitment to teach you the industry and develop invaluable sales and relationship skills.
Opportunity to grow into leadership role and build a team
Extra vacation day for your birthday when it falls on a weekday
All major American holidays off
10 paid vacation days after training period
5 paid sick days
Apply Now >>