CIO/ CISO Central & West Virtual Fireside Chat
February 17, 2022

Lessons Learned from the Log4j Exploit
Sonatype is the leader in developer-friendly, full-spectrum software supply chain management providing organizations total control of their cloud-native development life cycles, including third-party open source code, first-party source code, infrastructure as code, and containerized code. The company supports 70% of the Fortune 100 and its commercial and open source tools are trusted by 15 million developers around the world. With a vision to transform the way the world innovates, Sonatype helps organizations of all sizes build higher quality software that’s more aligned with business needs, more maintainable, and more secure.
Sonatype has been recognized by Fast Company as one of the Best Workplaces for Innovators in the world, two years in a row and has been named to the Deloitte Technology Fast 500 and Inc. 5000 list for the past five years. For more information, please visit Sonatype.com, or connect with us on Facebook, Twitter, or LinkedIn.
Speakers Include...

Austin Becker
Solutions Engineer
Sonatype

Sudhakar Namasivayam
Director of Software Engineering
Overstock

Amit Bhardwaj
CISO
Lumentum

Kunal Bhattacharya
Director, DevSecOps
American Family Insurance

Eduard Jooste
Sr. Director, Service Management Operations
Oportun
![]() Speaker: Austin Becker, Solutions Engineer, Sonatype
Speaker: Austin Becker, Solutions Engineer, Sonatype
Read Bio »
Austin is currently a Solutions Engineer at Sonatype where he is energized by helping people in digital transformation. Austin is passionate about helping people and teams learn and grow by striving for a deeper understanding of problems, establishing unique, innovative, and win-win solutions.
« show less
Invited Members Include...

Agenda
3:00pm-3:10pm (CST)
Opening Remarks & Executive Introductions
3:10pm-3:20pm (CST)
Host Introduction
3:20pm-4:00pm (CST)
Fireside Chat
4:00pm-4:30pm (CST)
Executive Discussion
Hosted by:

Title Representation
Industry Breakdown
Org. Size by Revenue
Got questions? We’ve got answers!
Why should I attend?
Your time is valuable and we make sure to make the most of it! We take the time to figure out your challenges and customize your experience to meet your needs. Our agendas are tailored to your feedback and we pride ourselves in covering the most cutting-edge content delivered by renowned industry experts. Look forward to building enduring partnerships and together we’ll go straight to the top.
Where is the event taking place?
The event is by invitation-only. The location will be released to all attendees once your registration has been confirmed.
What is the dress code?
We recommend business attire. Most attendees wear suits or comparable attire. Ties are optional.
Can I bring a colleague with me?
Yes! We always urge our members to refer their colleagues! We love adding new members to the community, especially if they come highly recommended by a current member. Either have them reach out to your Apex POC or have them fill out the Member Registration Form.
What if I have dietary restrictions?
No problem! Please let your Apex POC know as soon as possible in order for us to work with the venue on providing alternate options for you at the event.
What if I want to speak at an assembly?
Apex is always looking for speakers that can contribute their valuable insight. If you would like to speak, please contact your Apex POC or fill out the Speaker Registration Form on the Assemblies page. Please keep in mind that we receive many inquiries for speaking and sessions are available on a first come first served basis. But no need to worry, we have plenty of opportunities available at future assemblies.
I plan on being in attendance, but what if something comes up and I have to cancel?
We understand that something may come up on your calendar! Before canceling with us, please know that we will have a separate room for attendees to step out for work-related activities (meetings, emails, conference calls, etc.). If you must cancel, we just ask that you let us know at least 48 hours in advance so that we can open up the waitlist for another member.




















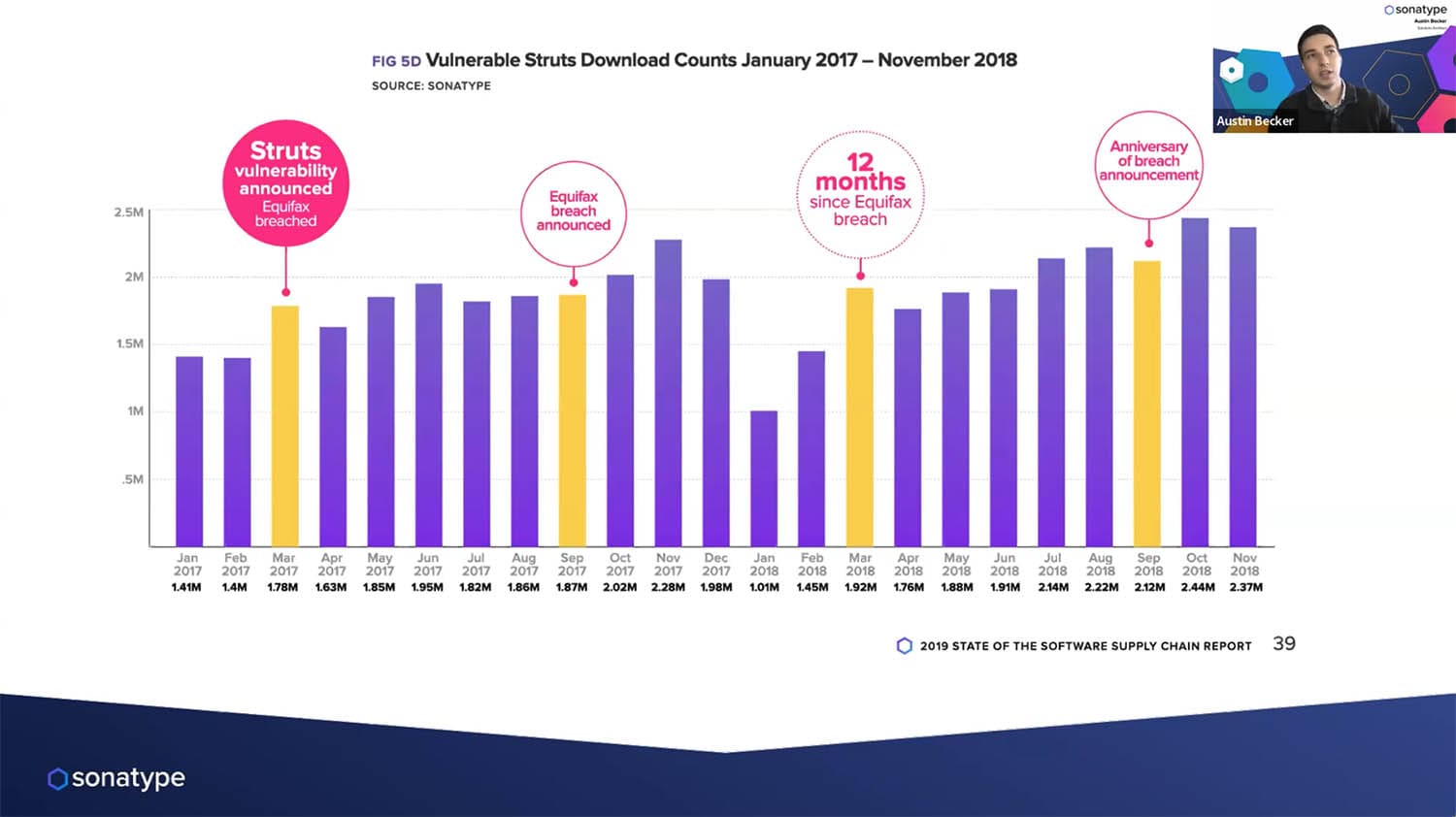
The Log4shell: vulnerability found in the Log4j logging framework has been recognized as one of the most critical vulnerabilities ever, open source or otherwise. And, while the dangers of the Log4j vulnerability remain high, the situation has highlighted an even bigger issue that is plaguing security professionals and developers: if you don’t know what’s in your software supply chain, you’re already behind.
When a flaw is disclosed, companies are instantly thrust into a race against time to fix it before it can be exploited by an attacker, meaning every minute counts. If you don’t know what’s in your software, you’re effectively giving hackers a huge head start.
While this outlook might seem bleak, there are easy steps you can take to significantly mitigate risk.
This session will help you do that by answering: