CIO/CISO North Central Panel
March 17, 2021
![]()
Securing the Software Defined Enterprise
Speakers Include...

Jonathan Nguyen-Duy
Vice President, Field CISO at Fortinet

Leon Ravenna
Chief Information Security Officer,
KAR Global

Kyle Forsyth
Cyber Security Engineer
Noblis

Paolo Vallotti
Global CISO Mondelez
![]() Speaker: Jonathan Nguyen-Duy, Vice President, Field CISO at Fortinet
Speaker: Jonathan Nguyen-Duy, Vice President, Field CISO at Fortinet
Read Bio »
Jonathan Nguyen-Duy is a Field CISO at Fortinet where he focuses on advising carriers, service providers and systems integrators on multi-domain risk management. With extensive experience in securing complex networks and hybrid-architectures, Jonathan is responsible for developing innovative solutions addressing the challenges of digital transformation – from edge-based computing to multi-cloud ecosystems. He specializes in security and governance issues pertaining to zero trust, insider threats, privacy, resilience and managed services.
Prior to joining Fortinet, Jonathan served as the Security CTO at Verizon Enterprise Solutions where he was responsible for strategic technology partnerships, the Verizon Cyber Intelligence Center, and the data science team that produces the annual Verizon Data Breach Investigations Report. His research experience spans root cause analysis of over 12,000 data breaches – providing great insight on effective risk management strategies.
Before that role, he led Managed Security Services and was responsible for data analytics and solutions supporting global enterprises and public sector agencies of all sizes. During this time, Verizon grew to become the industry’s largest and most analyst-awarded MSSP. A certified business continuity planner, Jonathan also developed Verizon’s resilience and advisory services.
Jonathan also served with the U.S. Foreign Service in Central America working on economic development and disarmament initiatives. He has more than 20 years of cybersecurity and BCDR/COOP experience – working through many business challenges including armed conflict, civil strife, labor strikes, natural disasters, terrorist attacks, network outages and a wide range of cyber incidents.
Jonathan is a widely published security expert and frequent speaker at industry conferences. He holds a BA in International Economics and an MBA in IT Marketing and International Business from the George Washington University.
Specialties: Cybersecurity, SIEM, SOAR, Data Analytics, Zero Trust, Artificial Intelligence, Machine Learning, CARTA, Physical Security, BCDR/COOP, Managed Services, Risk Management and Digital Transformation.
« show less
![]() Speaker: Leon Ravenna, Chief Information Security Officer, KAR Global
Speaker: Leon Ravenna, Chief Information Security Officer, KAR Global
Read Bio »
Leon Ravenna is Chief Information Security Officer at KAR Global. He leads KAR’s efforts in global security strategy, execution, and privacy and compliance services for the company’s more than 17,500 employees. A seasoned CISO, Leon has extensive experience in regulatory, compliance, and privacy, having managed ISO27001, HIPAA, SSAE-16, PCI, and NIST system builds and audits—in addition to holding a PMP. He is one of a very small group worldwide to hold six major Global Privacy certifications including CIPM, CIPP/ C and CIPP/ E, CIPP/ G, CIPP/ US, and FIP. Leon has more than 25 years of technology leadership experience in healthcare, financial services, and technology companies. He has also led nationwide support, web, and CRM development efforts, data center builds, and infrastructure for SaaS companies in the medical and financial space.
« show less
![]() Speaker: Kyle Forsyth, Cyber Security Engineer, Noblis
Speaker: Kyle Forsyth, Cyber Security Engineer, Noblis
Read Bio »
Mr. Forsyth provides over 15 years of experience designing and integrating technical cyber solutions for federal customers. He has a current CISSP, Certified Penetration Tester (GPEN), and has a Master’s degree in Information Security and Assurance. Kyle is knowledgeable and trained in multiple Cyber Domains including Cyber Analytics, Cloud Security, Cyber Forensics, Security Engineering, Risk and Compliance, and Offensive Security. He also has extensive experience as an ISSM/ISSO authoring and managing system policies, procedures, and Assessment & Authorization (A&A) packages for multiple customers and security programs.
Kyle also works regularly on Cyber Threat Hunting teams that leverage data science methods to look for threat-actor patterns and vulnerabilities in large amounts of log and PCAP data. Kyle has experience with various operating systems and many security tools like Kali, Wireshark, Nessus, Fortify, Zeek, FireEye, Cuckoo and several scripting languages. Mr. Forsyth also has experience with integrating system/software development best practices into projects using Python, Tableau, Spark, Hadoop, Hive, and D3.js.
« show less
Invited Members Include...














Agenda
10:00am-10:10am (CST)
Opening Remarks & Executive Introductions
10:10am-10:20am (CST)
Presentation and Industry Overview
10:20am-10:50am (CST)
CXO Panel Hosted by Sponsor
10:50am-11:30am (CST)
Executive Discussion
Hosted by:
![]()
Title Representation
Industry Breakdown
Org. Size by Revenue
Got questions? We’ve got answers!
Why should I attend?
Your time is valuable and we make sure to make the most of it! We take the time to figure out your challenges and customize your experience to meet your needs. Our agendas are tailored to your feedback and we pride ourselves in covering the most cutting-edge content delivered by renowned industry experts. Look forward to building enduring partnerships and together we’ll go straight to the top.
Where is the event taking place?
The event is by invitation-only. The location will be released to all attendees once your registration has been confirmed.
What is the dress code?
We recommend business attire. Most attendees wear suits or comparable attire. Ties are optional.
Can I bring a colleague with me?
Yes! We always urge our members to refer their colleagues! We love adding new members to the community, especially if they come highly recommended by a current member. Either have them reach out to your Apex POC or have them fill out the Member Registration Form.
What if I have dietary restrictions?
No problem! Please let your Apex POC know as soon as possible in order for us to work with the venue on providing alternate options for you at the event.
What if I want to speak at an assembly?
Apex is always looking for speakers that can contribute their valuable insight. If you would like to speak, please contact your Apex POC or fill out the Speaker Registration Form on the Assemblies page. Please keep in mind that we receive many inquiries for speaking and sessions are available on a first come first served basis. But no need to worry, we have plenty of opportunities available at future assemblies.
I plan on being in attendance, but what if something comes up and I have to cancel?
We understand that something may come up on your calendar! Before canceling with us, please know that we will have a separate room for attendees to step out for work-related activities (meetings, emails, conference calls, etc.). If you must cancel, we just ask that you let us know at least 48 hours in advance so that we can open up the waitlist for another member.



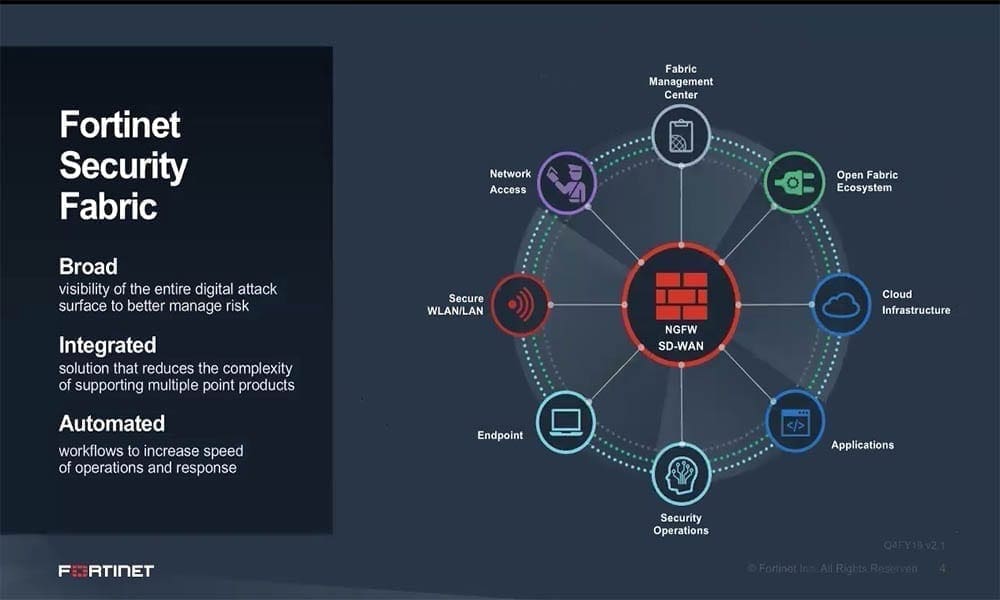
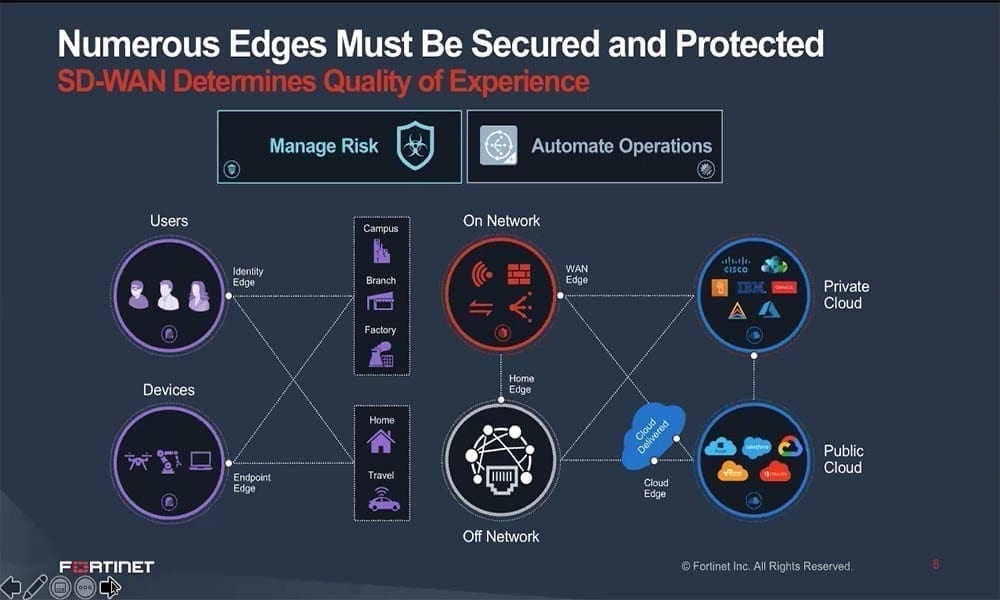
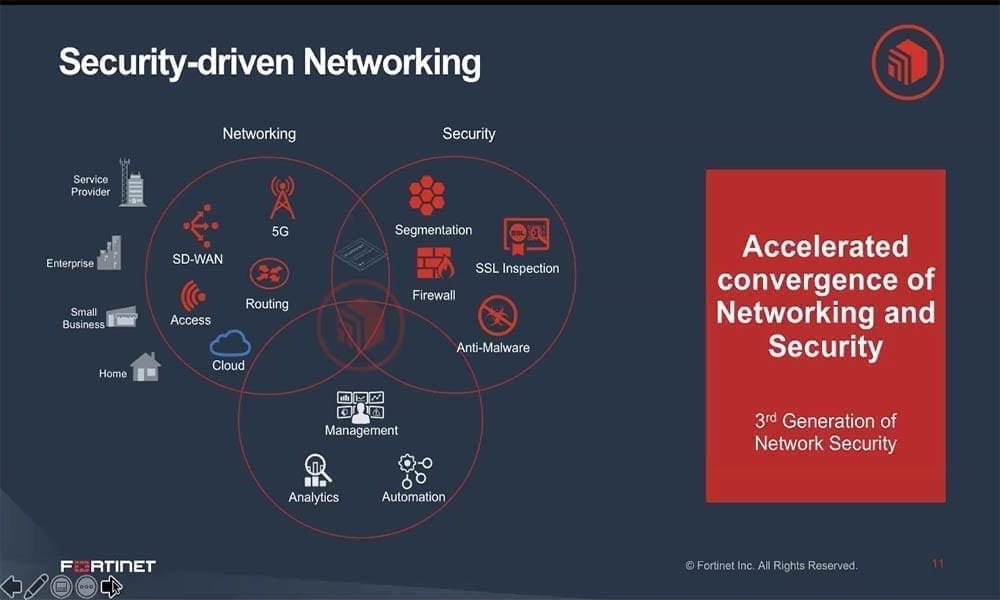
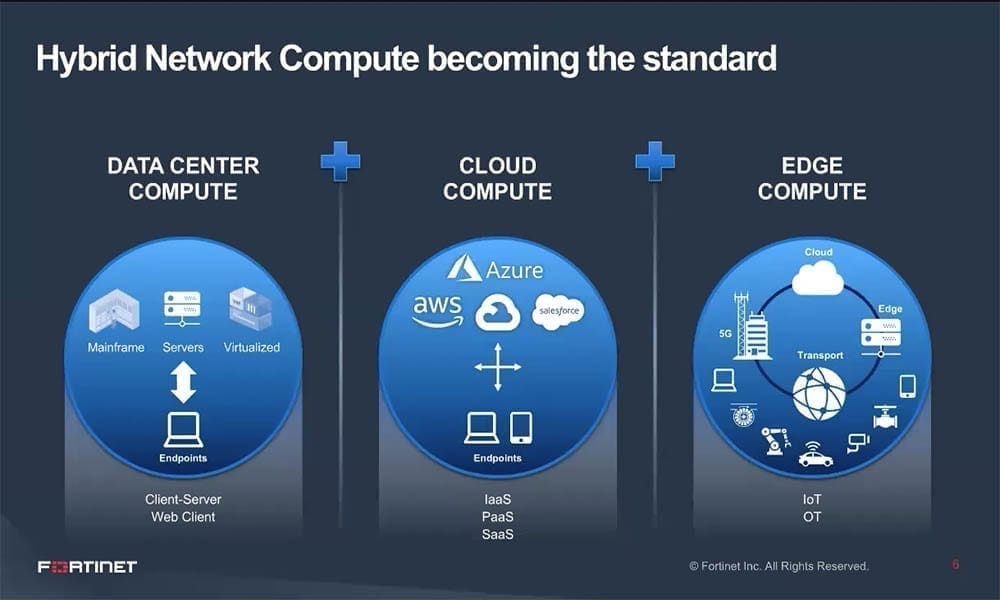
Organizations of all sizes are facing challenges arising from the shift to remote working and multi-cloud adoption which means that networks are increasingly more distributed and disaggregated than ever before. Simultaneously, we’re seeing the emergence of edge computing as the next tectonic shift in enterprise networking and Zero Trust becoming foundational to cybersecurity.
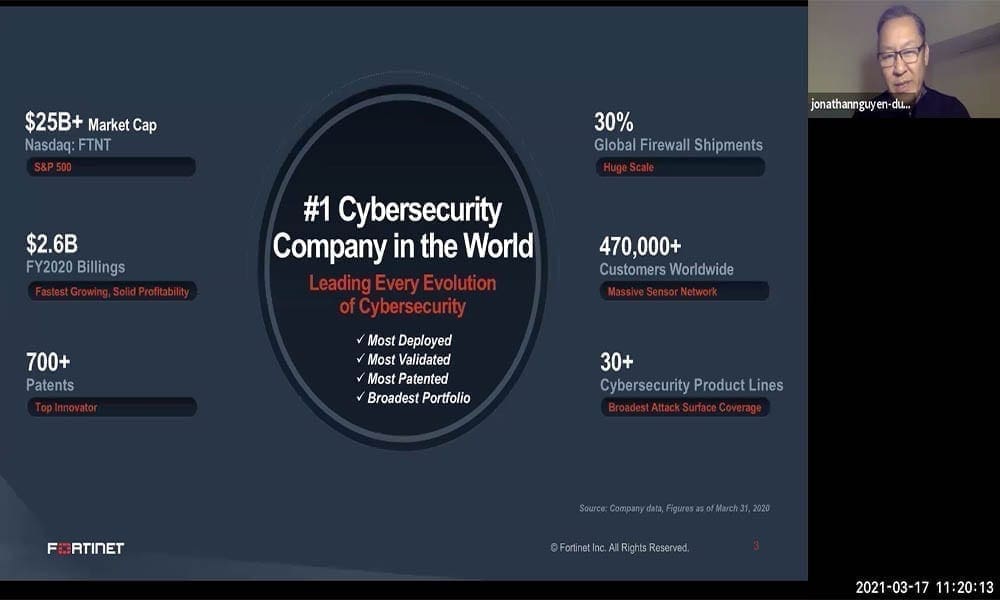
In this session, we’ll discuss how these macro trends are creating new challenges and opportunities for organizations of all sizes. How should we think about security and risk management service when enterprises own less and less infrastructure, platform and software? This is reflected in the evolution of the digital, virtual and software defined enterprise with its focus on service automation and value creation. We’ll review how integrated platforms like the Fortinet Security Fabric is ideally positioned as integrated prevention, detection and response technologies reach maturity, and the focus shifts to cross domain visibility and service automation.