CIO/ CISO Virtual East Panel
June 11, 2020

Security in the Digital Age
Speakers Include...

Sol Cates
Principal Technologist, CTO Office, Thales

Jay Duraisamy
SVP – USIS Engineering Leader, Equifax

Rod Aday
Director, Information Risk Management, Verizon

Timothy Swope
CISO, Catholic Health Services
About Thales Cloud Protection and Licensing
Today’s enterprises depend on the cloud, data and software in order to make decisive decisions. That’s why the most respected brands and largest organizations in the world rely on Thales to help them protect and secure access to their most sensitive information and software wherever it is created, shared or stored – from the cloud and data centers to devices and across networks. Our solutions enable organizations to move to the cloud securely, achieve compliance with confidence, and create more value from their software in devices and services used by millions of consumers every day.
We are the worldwide leader in data protection, providing everything an organization needs to protect and manage its data, identities and intellectual property – through encryption, advanced key management, tokenization, and authentication and access management. Whether it’s securing the cloud, digital payments, blockchain or the Internet of Things, security professionals around the globe rely on Thales to confidently accelerate their organization’s digital transformation. Thales Cloud Protection & Licensing is part of Thales Group.
Invited Members Include...













Agenda
12:30pm-12:40pm (EST)
Opening Remarks & Executive Introductions
12:40pm-1:20pm (EST)
CXO Panel Hosted by Sponsor
1:20pm-2:00pm (EST)
Executive Discussion
Title Representation
Industry Breakdown
Org. Size by Revenue
Got questions? We’ve got answers!
Why should I attend?
Your time is valuable and we make sure to make the most of it! We take the time to figure out your challenges and customize your experience to meet your needs. Our agendas are tailored to your feedback and we pride ourselves in covering the most cutting-edge content delivered by renowned industry experts. Look forward to building enduring partnerships and together we’ll go straight to the top.
Where is the event taking place?
The event is by invitation-only. The location will be released to all attendees once your registration has been confirmed.
What is the dress code?
We recommend business attire. Most attendees wear suits or comparable attire. Ties are optional.
Can I bring a colleague with me?
Yes! We always urge our members to refer their colleagues! We love adding new members to the community, especially if they come highly recommended by a current member. Either have them reach out to your Apex POC or have them fill out the Member Registration Form.
What if I have dietary restrictions?
No problem! Please let your Apex POC know as soon as possible in order for us to work with the venue on providing alternate options for you at the event.
What if I want to speak at an assembly?
Apex is always looking for speakers that can contribute their valuable insight. If you would like to speak, please contact your Apex POC or fill out the Speaker Registration Form on the Assemblies page. Please keep in mind that we receive many inquiries for speaking and sessions are available on a first come first served basis. But no need to worry, we have plenty of opportunities available at future assemblies.
I plan on being in attendance, but what if something comes up and I have to cancel?
We understand that something may come up on your calendar! Before canceling with us, please know that we will have a separate room for attendees to step out for work-related activities (meetings, emails, conference calls, etc.). If you must cancel, we just ask that you let us know at least 48 hours in advance so that we can open up the waitlist for another member.






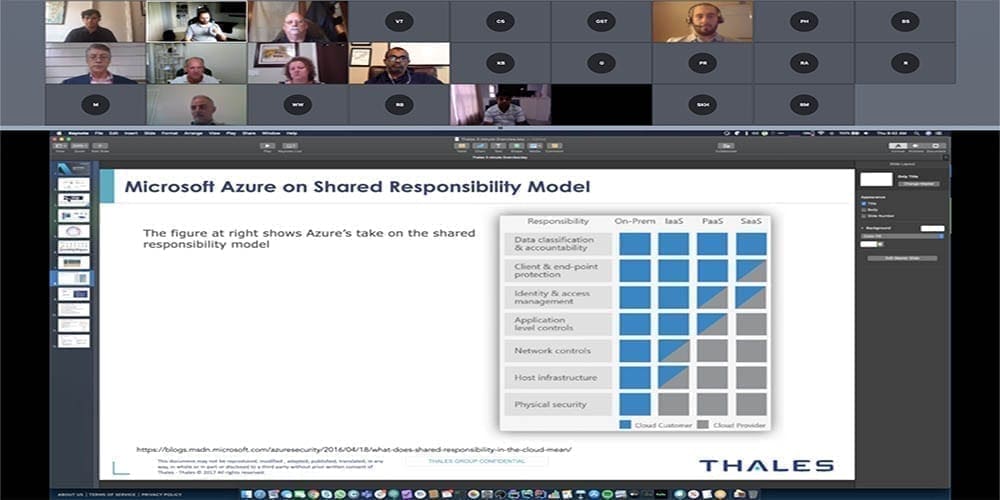
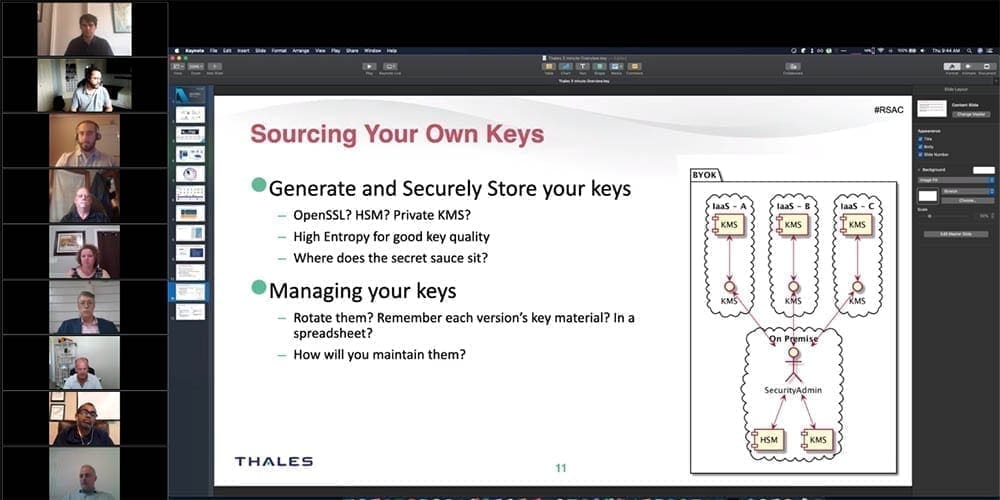
Cloud Key Management and Encryption… What’s really up with your data and those darn keys…
Keys have become the new contention point between service providers and their enterprise customers. As our collective industries have driven data security and encryption requirements into the Cloud Service Providers, they responded by enabling more security capabilities “IN the cloud” for the enterprise to control. However with that shared responsibility comes all the liability for the data that is controlled by the security controls. The CSP is in the business of providing security “OF the Cloud”, and we as enterprises, vendors, and industry experts are trying to manage these complexities across multiple CSPs.